When using MongoDB on AWS, it is recommended to use AWS IAM to manage access to MongoDB resources. This can be done through the use of IAM roles and policies.
To enable IAM authentication for MongoDB, the MongoDB instance needs to be configured to use the AWS authentication mechanism. This involves setting the authenticationMechanisms option to “MONGODB-AWS”. Once this is done, MongoDB will use the AWS authentication mechanism to authenticate users against the IAM service.
When a user attempts to access MongoDB resources, they will be authenticated by AWS IAM. If the user is authorized to access the requested resources, MongoDB will allow the access. If the user is not authorized, the access will be denied.
Below are the steps for authenticating the MongoDB Atlas Cluster using an IAM user or role.
Generate Secret and Access key
To generate an access key and secret key for an IAM user in the AWS Console, follow these steps:
- Log in to the AWS Management Console and navigate to the IAM dashboard.
- In the navigation pane on the left, click on “Users.”
- Select the user for whom you want to generate an access key and secret key.
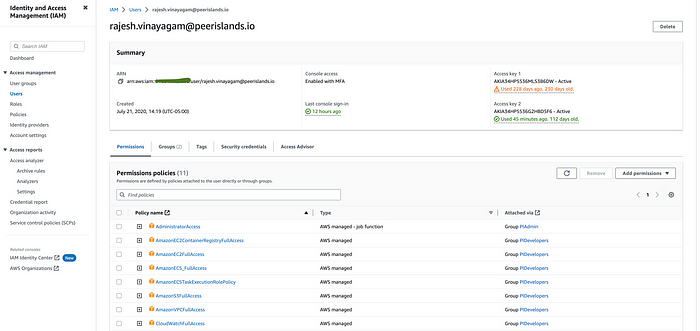
- Click on the “Security credentials” tab.
- Under “Access keys,” click “Create access key.”
- Click “Download .csv” to save the access key and secret key to your local machine.
- Store the access key and secret key securely, as they will not be displayed again in the AWS Console.
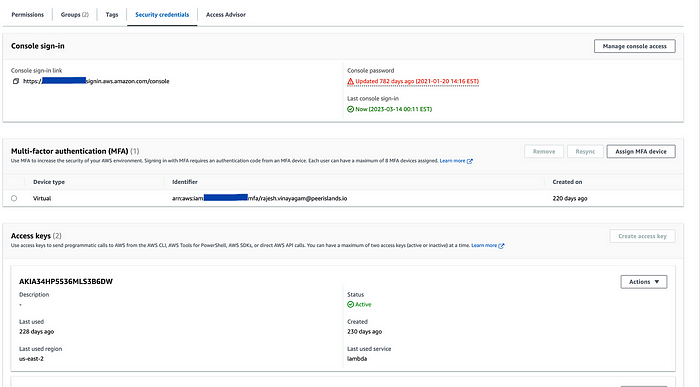
Note that the access key and secret key are used to authenticate API requests to AWS services. You should treat them as sensitive information and never share them with anyone. If you suspect that your access key and secret key have been compromised, you should immediately delete the access key in the AWS Console and generate a new one
Add Database User : AWS IAM User or Role
To add a database user in MongoDB Atlas for an AWS IAM user or role,
- Log in to your MongoDB Atlas account and navigate to the “Security” tab.
- Click on “Database Access” in the left navigation panel.
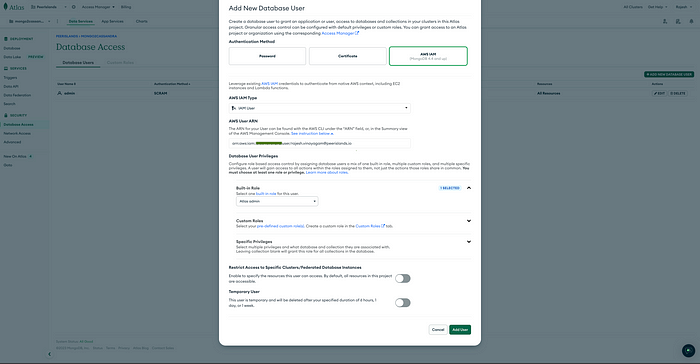
- Click on the “Add new database user” button.
- In the “Add new user” dialog, select the appropriate AWS IAM authentication method.
- For IAM database authentication, enter the AWS IAM user or role ARN in the “AWS ARN” field.
- Specify the desired database roles for the user. You can either select from the predefined roles or create a custom role.
- Click “Add User” to create the user.
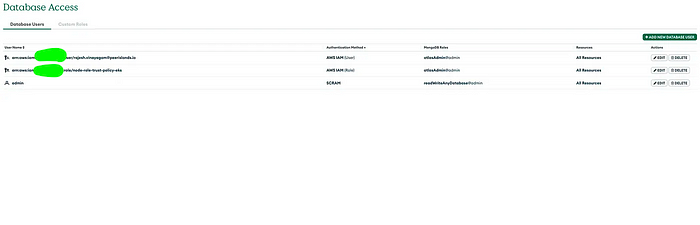
Once the users and roles are added they will be able to access the MongoDB cluster
Connection String
To obtain an IAM connection string from MongoDB Atlas, follow these steps:
- Log in to your MongoDB Atlas account and navigate to your cluster.
- Click on the “Connect” button.
- In the “Connect to Cluster” dialog, select “Connect with MongoDB Compass” and click “Copy.”
- Paste the copied connection string into a text editor.
- Replace the
<username>and<password>placeholders in the connection string with the AWS IAM access key ID and secret access key respectively. - If your IAM user or role requires an STS session token, add the
&authMechanism=MONGODB-AWSparameter to the end of the connection string. - Add the
&authSource=$externalparameter to the end of the connection string to specify the external authentication source.
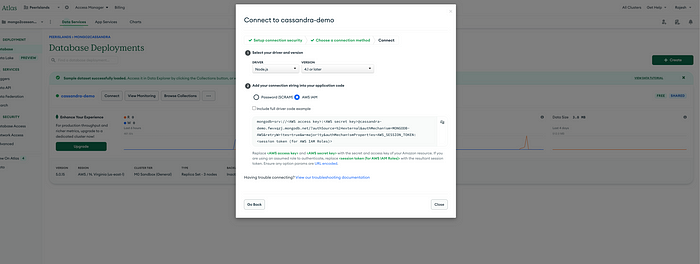
Your final connection string should be something like below
mongodb+srv://<AWS access key>:<AWS secret key>@cluster.ass.mongodb.net/
?authSource=%24external&authMechanism=MONGODB-AWS&retryWrites=true
&w=majority&authMechanismProperties=AWS_SESSION_TOKEN:<session token (for AWS IAM Roles)>
Security Token Service (STS)
Obtain temporary AWS security credentials for the IAM role. This can be done by using the AWS Security Token Service (STS) to assume the role.
aws sts get-session-token
{
"Credentials": {
"AccessKeyId": "AccessKey",
"SecretAccessKey": "secretKey",
"SessionToken": "sessionToken",
"Expiration": "2023-03-14T16:31:42+00:00"
}
}
Pass the temporary security credentials to your MongoDB client when connecting to the database. This can be done by setting the AWS_ACCESS_KEY_ID, AWS_SECRET_ACCESS_KEY, and AWS_SESSION_TOKEN environment variables, or by using a credential provider that automatically retrieves the temporary security credentials from the STS.
The AWS Security Token Service (STS) is a web service that provides temporary security credentials to users in order to access AWS resources. STS enables users to request temporary credentials that are valid for a specified duration and can be used to access AWS services and resources.
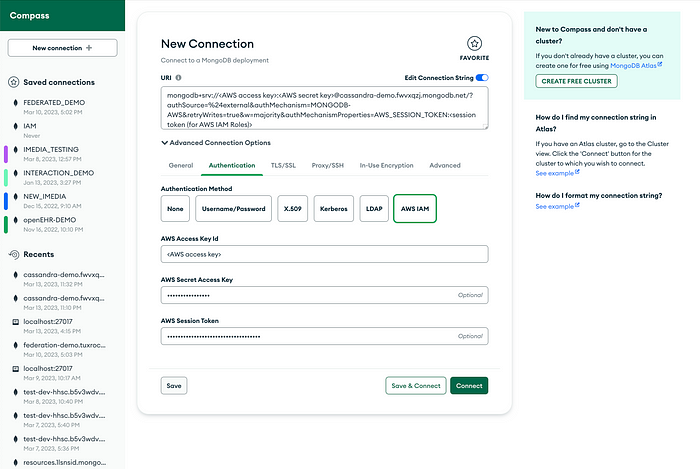
MongoDB Compass
Use your MongoDB client( Compass ) to interact with your MongoDB resources. With IAM authentication enabled, the client will be authorized with the temporary security credentials.
Conclusion
In this article, we looked at how to use an IAM user to authenticate a MongoDB instance. In the following article, we will go over how to authenticate MongoDB from an application running in ECS Fargate or EKS.
AWS + MongoDB provide limitless possibilities!


